What is Phishing? How this attack works and prevention against them?

Phishing is one of the most dangerous threats to organisations. The sender of a phishing mail pretends to be a trusted person or a system in order to steal valuable information.
Including personal identity data and credentials. A phisher uses both social engineering and computer technologies in order to steal valuable information.
If users take the bait and click the link, they’re sent to an imitation of a legitimate website. From here, they’re asked to log in with their username and password credentials. If they are gullible enough to comply, the sign-on information goes to the attacker, who uses it to steal identities, pilfer bank accounts, and sell personal information on the black market.
Phishing attack process
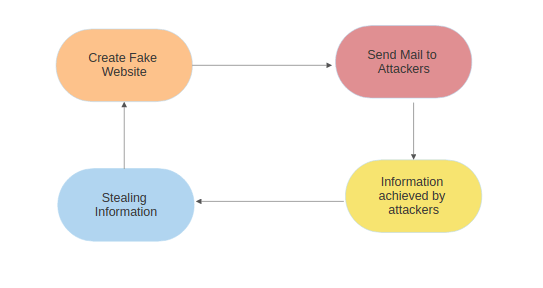
Phishing attack is carried out in 6 steps:
- Attacker obtains email addresses of their possible victims which he can send mail for several approaches.
- Attacker generates a phished page that seems like exactly equal as legal website.
- Phisher then ships mails having the hyperlink of a phished page to their scope of victims.
- Victim after receiving and analyzing the email and follow to the fake link for some personal gain or advantage.
- There he fills / enters his credentials and submits them.
- Attacker then thieve the private records and carry out their fraud including transferring cash from the victims account.
Prevention against phishing
An anti-phishing service is a technological service that helps prevent unauthorized access to secure and sensitive information. Anti-phishing services protect various types of data in diverse ways across a variety of platforms.
An anti-phishing service addresses a specific type of attempt to obtain personal or other sensitive information. Anti-phishing services provide anti phishing tools to help users recognize phishing and stealing of data. TIKAJ provides anti phishing solution, from monitoring & detection of phishing incidents, through to the site take-down incident response and resolution of an incident.
Several anti-phishing solutions provided are:
- MONITORING SPAMS: Spam is unsolicited email sent in bulk to unsuspecting users for commercial or malicious purposes. Monitoring spam and inbound communications are critical to good security practices.
- SOURCE CODE PROTECTION: Source code protection is important because if the code would be modified by malicious external attackers, secret backdoors may be added which can be catastrophic.
- MONITORING MALICIOUS WEBSITES: A malicious website is a site that attempts to install malware for anything that will disrupt computer operation, gather your personal information or, in a worst-case scenario, gain total access to your machine onto your device. Our automated systems scan known directories and standard directory structures, searching for hits on standard phishing filenames.
Feel free to contact us for more information







38 thoughts on “What is Phishing? How this attack works and prevention against them?”
Comments are closed.