DMARC Policy: Essential Guide

DMARC that stands for (Domain-based Message Authentication, Reporting, and Conformance) is a type of email protocol that uses SPF (Sender Policy Framework) and DKIM (Domain Keys Identified Emails). It controls the situation when email fails authentication tests. It is published at the side of domain.
Table of Contents
What is DMARC ?
DMARC, which stands for “Domain-based Message Authentication, Reporting & Conformance”, is an email authentication protocol. It builds on the widely deployed SPF and DKIM protocols, adding a reporting function that allows senders and receivers to improve and monitor the protection of the domain from fraudulent email.
DMARC makes it easier for email senders and receivers to determine whether or not a given message is the real email from the sender, and what to do if it isn’t. DMARC makes it easier to identify spam and phishing messages and keep them out of users, customers, and email inboxes. DMARC allows email senders and receivers to cooperate in sharing information about the email they send to each other.
If you want to remove the threat of direct domain spoofing, prevent spear phishing attacks then you must implement DMARC.
Why should you implement DMARC?
Here are three compelling reasons:
- Reputation: Publishing a record protects your brand by preventing unauthenticated parties from sending mail from your domain. In some cases, simply publishing a record can result in a positive reputation bump.
- Visibility: DMARC reports increase visibility into your email program by letting you know who is sending emails from your domain.
- Security: DMARC helps the email community establish a consistent policy for dealing with messages that fail to authenticate, making the email ecosystem as a whole more secure and trustworthy.
How it works ?
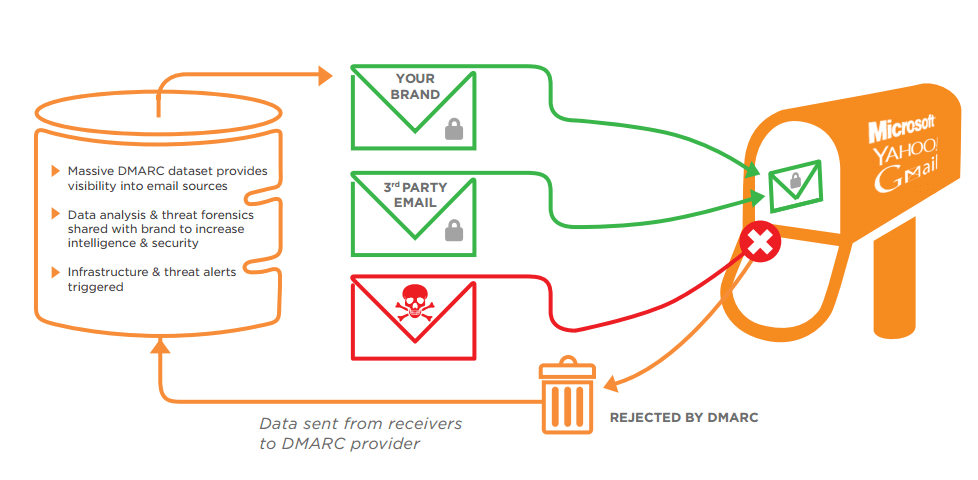
As mentioned earlier DMARC uses SPF and DKIM, these all components work together to authenticate the message and decide what to do with it. If any email fails authentication then the below process happens:
- The DNS owner publishes a DMARC for himself
- When the email is sent by the sender the recipient mail server checks for the DMARC record
- The recipient mail server performs the SPF and DKIM authentication in order to test if the sender is really the domain.
- After performing the above mentioned tests the receiver mail server sends the DMARC Aggregate Reports on outcome of the message received to the email address specified in the domain’s DMARC records.
DMARC protocol is essential as email is the primary source of communication in any business. It fights the malicious email practices the can put your business in risk. DMARC is used to safeguard the email phishing and scam practices.
SPF & DKIM – the prerequisites
SPF
SPF is a DNS text entry which displays a collection of servers that should be permitted to send mail for a specific domain. It enforce the principle that the list of people is authoritative for the domain, since the owners/administrators are the only people allowed to add / change the key domain. Hosts are permitted to use a particular domain name is published in the Domain Name System (DNS) records for that domain, as a TXT record. Mail receivers can use that records to check the authorisation. SPF’s advantage is the receiver can then use the sender’s domain to determine email acceptance or rejection.
DKIM
DKIM is a signature-based Email Authentication technique. It is the result of merging the DomainKeys and Identified Internet Mail specifications.It allows a domain owner to tag and email message with a digital signature. Verification of the email is done using the signer’s public key, which is published in the DNS. A valid signature ensures that at some part of the email have not been modified since the signature was attached.
DMARC has three settings: monitor; quarantine; and reject, and organisations decide how they want to hande unauthenticated emails.To know more about how DMARC works, check out our blog on DMARC.
How it protects organization from Phishing?
- DMARC confirms if the received email is real or not. Before DMARC it was unstable as some of the legitimate mails are tagged in spams.
- DMARC creates consistency for dealing with messages that fail to authenticate.This helps the mail ecosystem as a whole become more secure and more trustworthy.
- Publishing a DMARC record protects brands reputation by stopping unauthorised hosts from sending mail on behalf of your domain.
- DMARC reports give you visibility of who is sending mail from your domain.
- It increases control and security.
Implementing DMARC on your organization’s mail servers domains is the first step to protecting your enterprise from phishing attacks. To ease up the implementation we offer DMARC+ solution, which provides easy implementation dashboard which can your journey easy.
DMARC Deployment Steps
If you want to deploy DMARC, it’s recommended to ramp up slowly by employing policies in a specific order. Here’s a conservative DMARC deployment cycle:
- Monitor all
- Quarantine 1%
- Quarantine 5%
- Quarantine 10%
- Quarantine 25%
- Quarantine 50%
- Quarantine all
- Reject 1%
- Reject 5%
- Reject 10%
- Reject 25%
- Reject 50%
- Reject all
Start by monitoring your traffic and looking for anomalies in the reports. Then, move on to changing the TXT record policy setting from “none” to “quarantine.” Review the results, both in your spam catch and in the daily DMARC reports. Once you’re sure all of your messages are signed, change the policy setting to “reject” to make full use of DMARC.
To stage and sample your DMARC deployment, use the optional pct tag. Since 100% is the default, passing “pct=20” in your DMARC TXT record results in one-fifth of all messages affected by the policy receiving the disposition instead of all of them. This setting is especially useful once you elect to quarantine and reject mail. Start with a lower percentage, and increase it every few days.
As always, review your daily reports and attempt to remove the percentages as quickly as possible to complete the deployment. Remember, the ultimate goal is to make full use of DMARC by rejecting all unauthenticated messages. By following these deployment steps and reviewing reports, you can make your email ecosystem more secure and trustworthy.
How can I tell if DMARC is making a difference?
A day or two after a domain owner publishes the simplest monitoring-mode DMARC record in DNS, they will begin to receive reports from DMARC receivers with statistics about email sent to them using the domain owner’s domain. In other words, if you own or operate example.com and publish a DMARC record requesting reports, you will get statistics on all messages that claim to come from your domain from all DMARC receivers. So, you will suddenly be able to see how many fraudulent messages are using your domain, where they’re coming from, and whether or not they would be stopped by a DMARC “quarantine” or “reject” policy. The report from each receiver is an XML file that includes the following fields:
- Every IP address using your domain to send email
- A count of messages from each of those IP addresses
- What was done with these messages per the DMARC policy shown
- SPF results for these messages
- DKIM results for these messages
Usually, DMARC Solution’s client portal provide reports which provide a great deal of insight into the health of your message streams.
Limitations of DMARC
DMARC is a great solution for preventing direct domain spoofing. When an email is sent by an unauthorized sender (whether it is sent by a malicious user, or even an unauthorized user of a department of the company that owns/operates the domain), DMARC can be used to detect the unauthorized activity and (if so configured) request that those messages be blocked or discarded when they are received.
If the owners/operators of website.com use DMARC to protect that domain, it would have no effect on website.net, unless .NET is also DMARCISED. Impersonating a given domain is a common method used for phishing and other malicious activities, there are other attack vectors that DMARC does not address.
DMARC does not address cousin domain attacks (i.e. sending from a domain that looks like the target being abused – e.g. website.com vs websit3.com ), or display name abuse where the “From” field is altered to look as if it comes from the target being abused.
Conclusion
In conclusion, DMARC is an effective way to protect your email domain from malicious practices such as domain spoofing and phishing attacks. With the right deployment plan, you can gradually ramp up your DMARC usage and make your email ecosystem more secure and trustworthy. For expert consultancy on designing a deployment plan for your email infrastructure, feel free to contact us.
To learn more about DMARC, click here to read similar articles curated by us.







4 thoughts on “DMARC Policy: Essential Guide”
Comments are closed.