Know-How : We Fought back a Spear Phishing Attack in 6 Easy Steps!

Like every phishing campaign, spear-phishing campaigns are also used to fetch and collect your sensitive information, credentials and ask you to click legitimate-looking malicious links.
Phishing is not a new term that you are hearing for the first time and with advanced and sophisticated email security tools they are no longer able to fool wary individuals. Hence, threat actors are every day employing new tactics to fool people and Spear Phishing is one such attack type that has proven to be lucrative enough to fool people.
What is Spear Phishing Attack?
Identity Masked, message tailored, legitimate sender, an urgent request? Guess what it is: a Spear Phishing Target Email.
Your website is your brand image online and a gold mine for attackers to know about your organization. A few small surface searches and they know all the nitty-gritty of your organization, be it the name of your employees, their position, the hierarchy chain, or even the jargon you use to interact with them. These details may be of little to no value for you but these little sprinkles are served to you in a manner that increases the authenticity of an email. Sounds dangerous, right?
Why is Spear Phishing Rising?
Spear Phishing is on the rise because THEY WORK. With a basic understanding of phishing emails, anyone can understand that the email is dubious but what makes spear phishing work is their detailed approach, they are targeted and that increases their authenticity by 10x. What makes them stand out is that traditional security defenses can’t detect and flag them, these emails come into your inbox and not your spam folders.
A normal phishing email blankets a company’s entire database however Spear Phishing Email targets a specific individual in a specific organization with a specific/clear mission to accomplish. Spear phishing is one of the most prevalent APT attacks. The return on an APT attack is a lot higher because of its precision and expertise, cybercriminals put a lot of homework before they launch one. So, stay vigilant.
Now comes the main part, Here is what happened to us
One of our employees was acquainted with a similar spear-phishing attack where the attacker planted a seed of “Helping someone” in the email. We all want to practice kindness and help someone in need and especially if there is something urgent and the tendency to help increases when the help is coming from someone within your organization. Though the employee cautiously followed a few simple steps which we will discuss later in the blog and the employee successfully fought back the attack, not everyone can be that cautious every time.
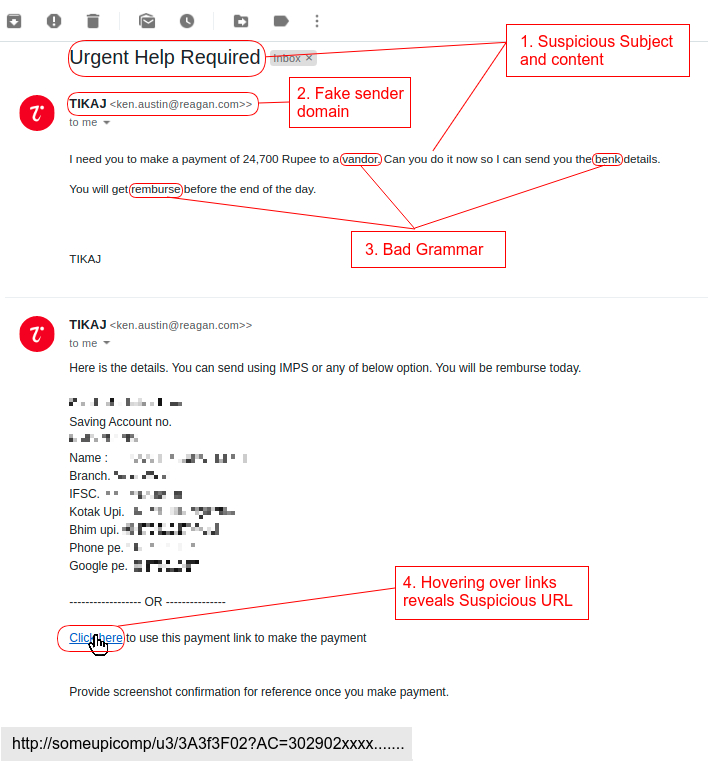
If you receive an email like this, do the following!
At home: Delete
At work: Follow the predefined policies, if you’re still skeptical about something, ask someone for help immediately!
Stay Safe Online
These few simple steps can keep your organization safe.
- Implement DMARC Authentication: Implementing DMARC can protect your customers from spam, fraud, spoofing, and phishing by simply blocking unauthorized access to your domain, you can also get comprehensive information about who (and/or what) across the vast internet is sending an email using your domain. It’s always better to have the best defense in place to protect yourself from identity theft and targeted attacks.
- Train Employee: With Spear Phishing on the rise implementing the best technique is not the only thing you need, a combination of training modules for employees along with simulated (yet harmless) phishing attacks within your team and providing them first-hand training can stop the Human Hack. Security awareness training will help employees be wary about what they open and click.
- Review Internal Policies: Make sure you have internal policies and procedures defined in case of an attack. Every employee should know what are the steps they need to take if they are phished, don’t judge them rather make them feel comfortable so that they don’t hesitate in reporting the attacks.
- Multi-Layer Defense Approach: As a last line of defense, MFA requires additional information during login to thwart criminals trying to access your data using stolen credentials. The concept of “Defense in depth” is something we need to inculcate immediately. Protect all endpoints for a full-proof defense.
- Audit Your Security Posture: Doing a regular audit in your security posture helps you identify the security gaps and voids that need to be addressed before a major attack happens.
- Keep A Check On Your Online Presence: If there is anything that you’ve put online that can be used for a potential attack take it down, reconsider every information that you put online because YOUR WEBSITE IS THEIR GOLD MINE.
Bonus Tip:
Here is what our employee did and
You Can Also Follow These Guidelines While You Read An Email
There is no single technique to protect you and your organization from phishing attacks, but here are a few things you can do:
There is no particular technique or magic formula to protect you and your organization from phishing attacks, but here are a few things you can do:
- Check the name and email address cautiously. Are there any peculiar letters, names, or numbers?
- Drift your cursor over the links to ensure they go where you believe they should be going.
- Check for erroneous language and spelling. Is it inadequately composed?
- Be careful of any email that creates any type of urgency, fear, or helpful needs.
- Be extra cautious if there are any requests for money or personal/confidential information.
- At last, on the off chance that you see or feel anything uncommon or dubious with regards to an email, set aside the effort to contact the sender for verification.
Covid-19 and Spear Phishing Threat, Read here: https://www.firstpost.com/tech/science/covid-19-vaccine-related-spear-phishing-attacks-have-increased-after-the-release-of-the-vaccine-9398971.html






